If any SPHTM faculty, student, or staff has a security concern, relating to an account or device, please contact SPHTM-IT:
- Phone: (504) 988-2685
- Email: sphhelp@tulane.edu
SPHTM-IT works in close relation with the Tulane University Information Security Office (ISO). The mission of the Information Security Office (ISO) is to support the mission of Tulane University by assuring confidentiality, integrity and availability of its information and information systems. This mission is accomplished through implementing assurance methods that protect and defend these assets by:
- focusing on reducing the risk to these systems;
- complying with applicable policies, laws, and regulations;
- raising the conscientiousness of the University community through awareness, training and education; and
- working with departments to evaluate and improve their computer security practices.
FDE Enforcement
All workstations that contain or work with TUMG owned data are required to use Full Disk Encryption (FDE). Software used for full disk encryption will meet standards established by FIPS, HIPAA and HITECH and Tulane Information Security and will be available through and supported by Tulane Encryption Services.
Device Standards
Devices that require Full Disk Encryption are required to meet minimum standards as set forth by both the vendor and Tulane Information Security. These standards will be available to Faculty and Staff for review and will include requirements for hardware, operating systems and expectations of a healthy computing environment.
Frequently Asked Questions (FAQs)
Below are the common questions the Information Security Office receives regarding Full Disk Encryption (FDE). Please contact us if you need additional information or have other concerns.
What is SecureDoc?
SecureDoc is a comprehensive full disk encryption product that secures data at rest (DAR). It has two main components: the client software used to encrypt and decrypt data and the server software used to configure, deploy and manage laptop encryption, desktop encryption and server encryption and external devices encryption for an entire organization.
The SecureDoc client software uses a FIPS 140-2 level 1 and level 2 certified AES 256-bit cryptographic engine to encrypt data. WinMagic recommends that all drives be protected with full-disk encryption (FDE), container, and volume encryption can be used to supplement FDE on shared laptops, desktops and servers to add another layer of defense for classified data, and to encrypt data on external storage devices such as USB keys, CD/DVDs, and SD cards. The SecureDoc client software provides encryption capabilities on multiple operating systems (Windows, Mac, and Linux via SecureDoc OSA).
What operating systems are supported?
SecureDoc supports Windows 10 and macOS.
While earlier versions of Windows are supported, the Information Security Office highly recommends Windows 10 as a minimum requirement for PC devices.
Will full disk encryption slow down my machine?
No. Encryption runs as a background task that uses negligible system resources. While the initial encryption process is taxing on computer resources as it is encrypting all data on your physical drives, subsequent encryption takes place as a normal operation of writing data to the physical drive.
Will full disk encrypiton protect me from viruses and other malicious software?
No. Full Disk Encryption’s only function is to protect the data on a computer if it becomes accessible by a third party who does not have the credentials to log on to the machine. The operating system itself acts as normal otherwise and should still run anti-virus software and requires the same concern from the customer when avoiding malicious websites and emails.
Will full disk encryption destroy all the data on my workstation?
No. Full Disk Encryption is a safe product meant to protect information at rest on a device if it is lost or stolen.
The Information Security Office highly recommends that all staff and faculty consult their department in regards to the required back-up and recovery strategy solution recommended for them.
Will full disk encryption work with my self encrypting drive?
Yes. SecureDoc supports SED technology as an escrow service of the drive encryption key. With key escrow we can offer support if your drive needs unlocking.
Will full disk encryption work with bootcamp or dual boot technology?
No. Full Disk Encryption requires an environment that allows it to manage the boot sequence in order to protect your data at rest.
The Information Security Office highly recommends that all customers consider virtual machine software to manage multiple operating systems. VMWare is available for free to staff and faculty through the e-academy website and Technology Services is able to provide valid licensed copies of windows for installation into a VM.
Tulane processes just under five million email messages every day accommodating approximately 70,000 personal and resource accounts. Technology Services dedicates significant resources to filter these messages for spam and phishing because we understand that phishing and spam are both annoying and potentially dangerous. We have to balance the task of blocking malicious email while not blocking legitimate traffic. Implementing much more restrictive filtering rules might result in blocking emails that Tulane customers need.
Tips To Not Get Phished
- Never send your password in an email.
- If it’s suspicious report it to security@tulane.edu.
- Hover over links with your mouse cursor to find suspicious links.
- Watch for warning signs like EMERGENCY or URGENT that are meant to scare you into responding.
- Tulane will never ask you for your password!
Microsoft Filtering
Technology Services works closely with Microsoft to filter incoming messages. Read the details here.
When phishing and spam do get through, we notify Microsoft with the relevant information. Users can assist by sending any offending message along with header information to security@tulane.edu.
See this Knowledge Base article for instructions on how to locate the header information in an email message.
Compromised user accounts - Protect your account credentials
In many cases the phishing messages that are getting through to users are the result of a compromised Tulane account – a student, faculty or staff member unwittingly gives up his Tulane password to a scammer, who then uses that legitimate Tulane account to spam or phish other Tulane users. The scammer will change the user’s password, lock him/her out of the account, and send phishing messages to thousands of Tulane recipients in seconds.
Access to other systems
Once a scammer has your credentials, they also have access to other important systems such as Canvas, Gibson, Box, and every other system that accepts a Tulane username and password.
More About Phishing
See the following Knowledge Base articles related to phishing and secure computing:

Technology Services is pleased to offer Tulane faculty, staff, students, and affiliates access to security awareness on-line training. These interactive modules make it easy to keep yourself safe online, to protect your data, and stay on top of security issues.
These short and informative modules cover HIPAA, FISMA and FERPA standards as well as important topics such as Social Networking and Mobile Device Security. These videos are helpful for anyone who uses a computer.
These easy to use training tools are available through the Training Wave at Gibson online:
- Log in to gibson.tulane.edu
- Click on your role (student, faculty, staff)
- Click on "Training Wave" in the left-side menu
- Click on "Course Catalog"
All courses with Course IDs beginning with "TIS" are part of the security awareness training series
Every user of Tulane University's information systems resources is responsible for protecting the confidentiality, availability and integrity of the University's information assets.The Information Security Strategy supports and coordinates our university community's efforts to secure Information and Information Systems from unauthorized access, disclosure and disruption. The document outlines Information classification; roles and responsibilities for protecting information; and provides a high level strategic overview of administrative, operational and technical controls that should be implemented to safeguard the University's information assets.
Summary of control requirements:
- Implemented controls should ensure the availability, integrity and confidentiality of the University's information resources
- Roles and responsibilities for information use should be appropriately segregated to ensure users have access to information on a need to know basis only
- Audit logs and trails should be maintained for all applications and systems that handle and maintain sensitive University information
Asset Classification
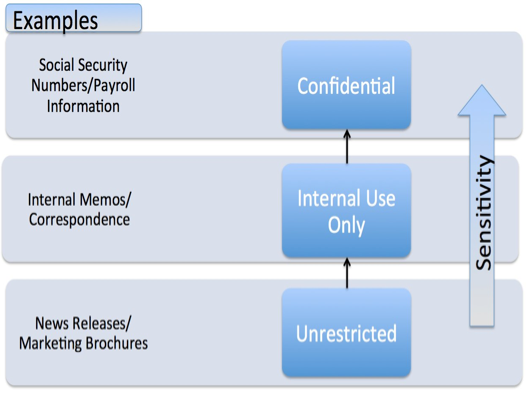
To assist in the appropriate handling of information, a sensitivity classification hierarchy should be used throughout Tulane University. This sensitivity classification system ensures consistent handling of information regardless of form, mode of transmission or storage.
The information classification categories are:
- Confidential – Covers sensitive information about individuals and the University. It requires a high level of protection against unauthorized use, disclosure, modification and destruction.
- Internal Use Only – Covers information that requires protection against unauthorized disclosure, modification, destruction, or use, but the sensitivity of the information is less than that for confidential information.
- Unrestricted – Covers information that can be disclosed to any person inside or outside the University. Although security mechanisms are not needed to control disclosure and dissemination, they are still required to protect against unauthorized modification and destruction of information.
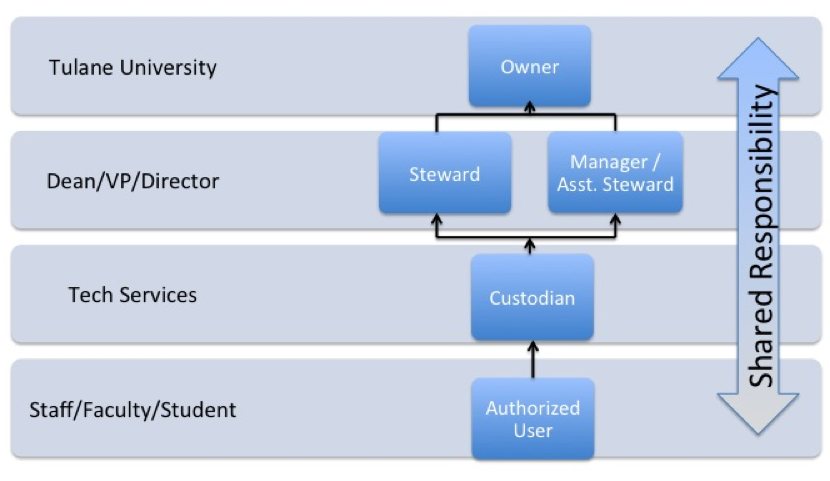
Roles and Responsibilities
As a member of the University community, you share in the responsibility for protecting information resources for which you have access or custodianship. In addition, there are particular responsibilities assigned to specific groups.
These specific groups are:
- Owner – The University is considered the OWNER of all university information.
- Steward/Assistant Steward –Those members of the University community who have the primary responsibility for a particular subset of information and perform the duties of the information owner on behalf of the university.
- Custodian – They are in physical or logical possession of information and/or information system assets and are responsible for the day-to-day operations, maintenance and safeguarding of those assets.
- User – This includes all university community members who are authorized to use any University information resource.